Network Troubleshooting: Consider The Load Balancer

Which Mode?
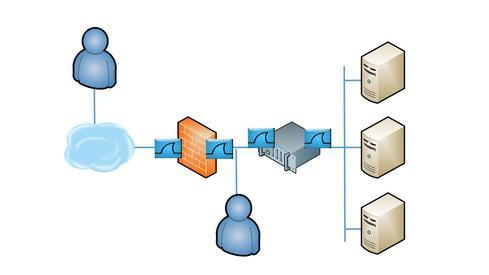
Multiple Vantage Points
Now you are ready to take the trace files aka pcaps. In a perfect world, you would have taps to insert at each of the points in the diagram below. If you don't have taps, you can capture traffic using a SPAN or mirror port on the switch. Or you can use tcpdump on the inbound and outbound ports of the firewall and load balancer. The key is to capture packets in all four places at one time to look at conversations from four different vantage points.
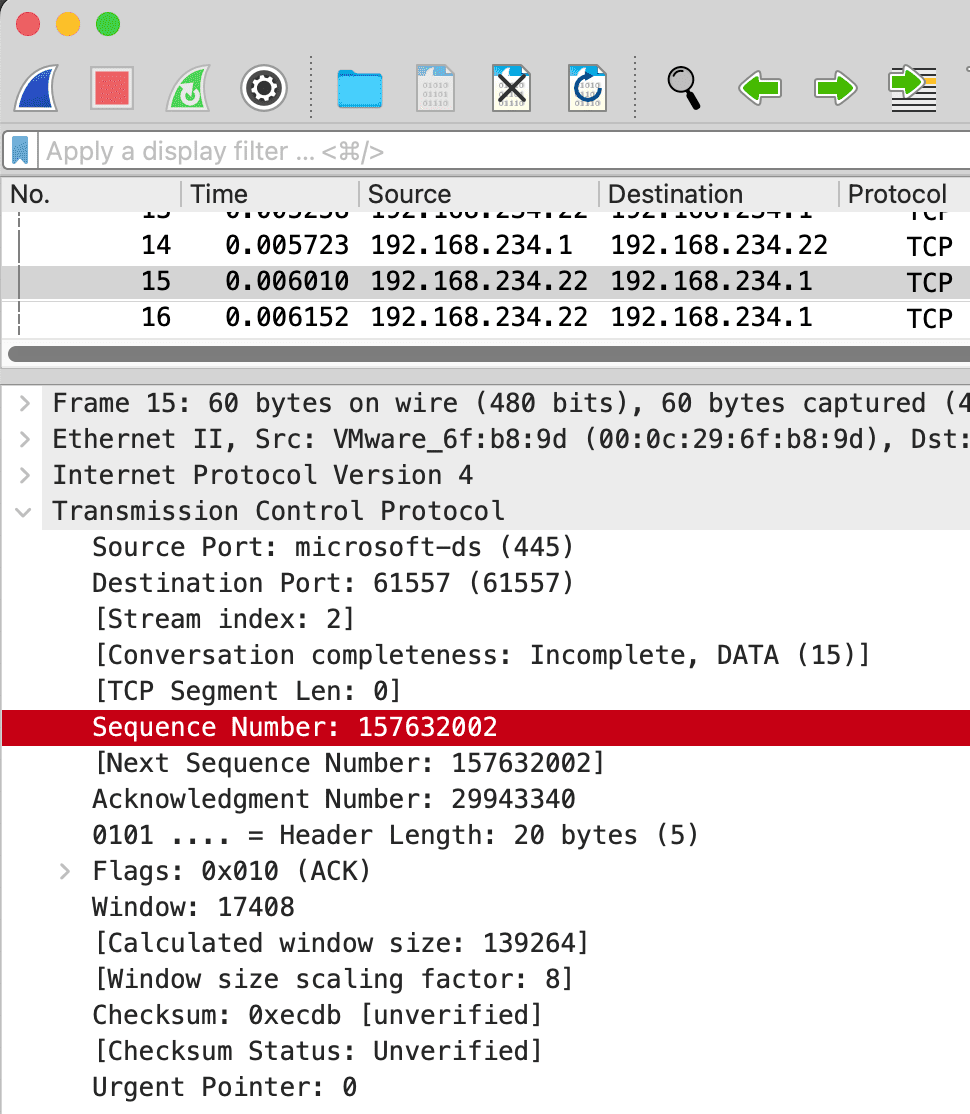
Filter for Unique Fields in Each PCAP
The tricky part comes in if your load balancer creates its own packets on the NAT side to the server. The TCP sequence field would then no longer be the same from end to end. The best field to use in that scenario is one that is unique in the application layer. For HTTP, I recommend the Cookie field, and for HTTPS, the Random Bytes field in the Client Hello.


